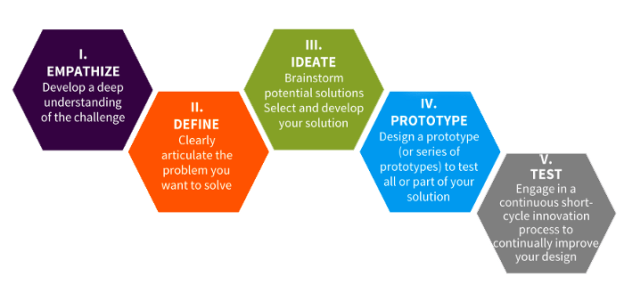
Over the last few weeks I’ve been exploring the habits of successful journalists that are often described as being “innate” or “unteachable”: from curiosity and scepticism, persistence and empathy, to creativity and discipline. In this final post I look at a quality underpinning them all: passion.
Are journalists only ever born with a passion for their craft — or is it something that can be taught?
Of all the seven habits that have been explored in this series, passion is perhaps the one that seems most innate — a quality that you “either have or don’t have”.
Can we teach passion? Well, we can provide the reasons why someone might be passionate about their craft — we can inspire passion and we can create opportunities to experience the things that have stimulated passion in others. Continue reading